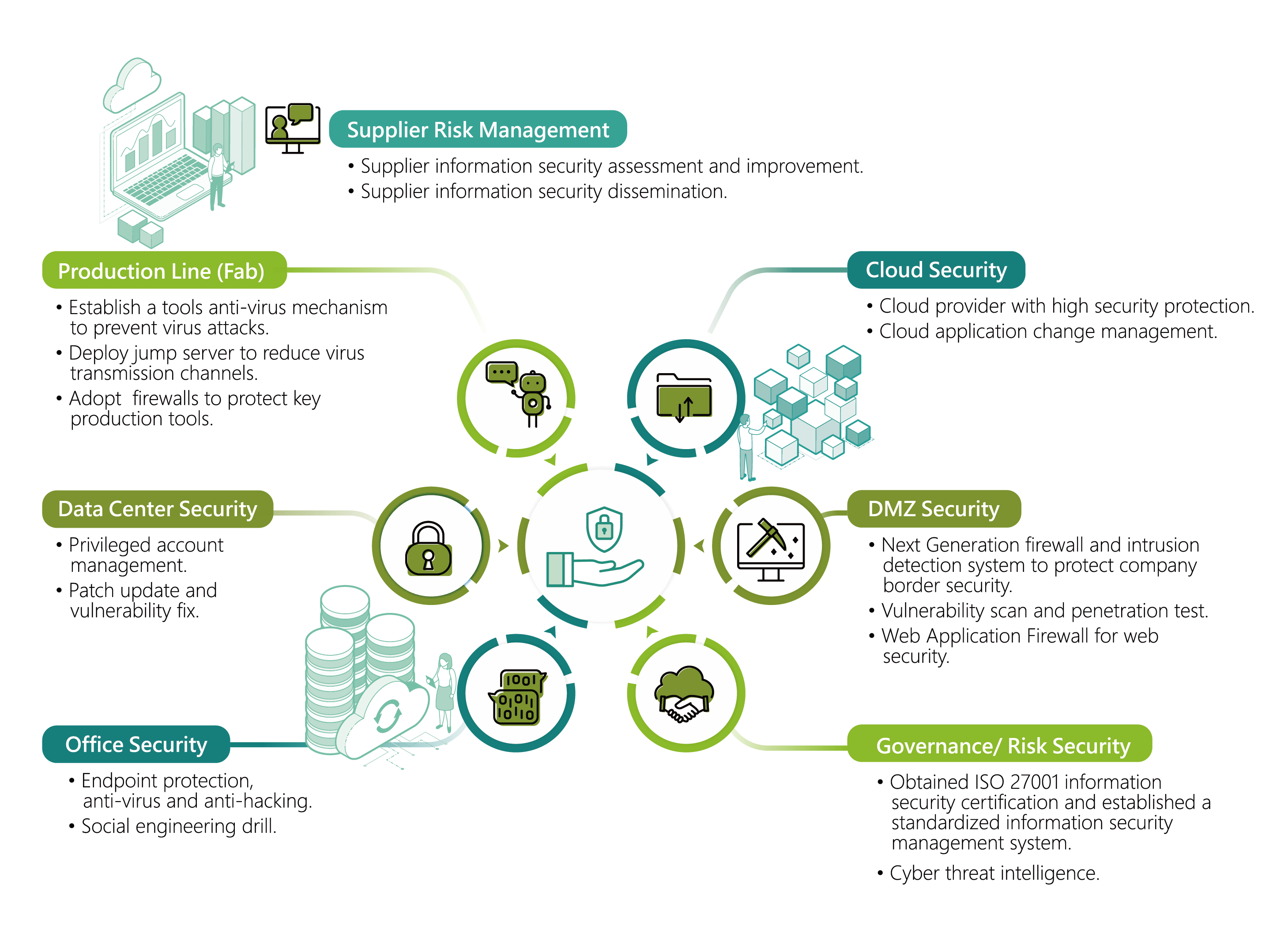
To strengthen information security, VisEra uses the six major aspects including cloud security, Demilitarized Zone (DMZ) security, information security governance, office area security, data center security, and production line and supplier security to strengthen the defenses for information security.
To effectively monitor information security intelligence, the Information Security System O&M Unit of VisEra’s Information Technology Department uses the information security products and intelligence of renowned domestic and foreign companies such as Fortinet, TrendMicro, Crowd Strike, Palo Alto Networks, and Proofpoint. It established the Security Operation Center (SOC) in 2020 to monitor changes in the internal information security environment, actively detect information security problems, and take response measures for data centers, anti-virus protection, networks, operating systems, applications, and production line machine protection. We also work with the Science Park Information Security Sharing and Analysis Center to collect, exchange, and analyze information on information security risks for critical infrastructure. We monitor potential security threats and vulnerabilities and address the vulnerabilities to prevent potential threats with the security intelligence we obtained and reduce the risks of major information security incidents. After the establishment of the SOC, it monitors the use of the Internet, gateways, servers, and terminals each day. If it identifies suspected attacks from an external IP, it blocks the source IP. In 2022, we implemented CrowdStrike’s Managed Detection and Response (MDR) service to assist in monitoring the office computers and IT server rooms for any malicious software implants. Using cloud-based machine learning, it helps detect and prevent the execution of malicious programs. Since its implementation, the system has successfully blocked 247 instances of medium to high-risk malicious programs. Furthermore, there were zero cybersecurity incidents reported in 2022.
To ensure compliance with the Company’s Proprietary Information Protection Policy, the Proprietary Information Protection Officer (PIP Officer) inventories and classifies sensitive information such as proprietary information and personal data within the Company. Each unit sets up a special folder for personal data protection in the shared space with restricted data access and encryption. The PIP Officer performs quarterly self-audits to protect proprietary information and personal data.
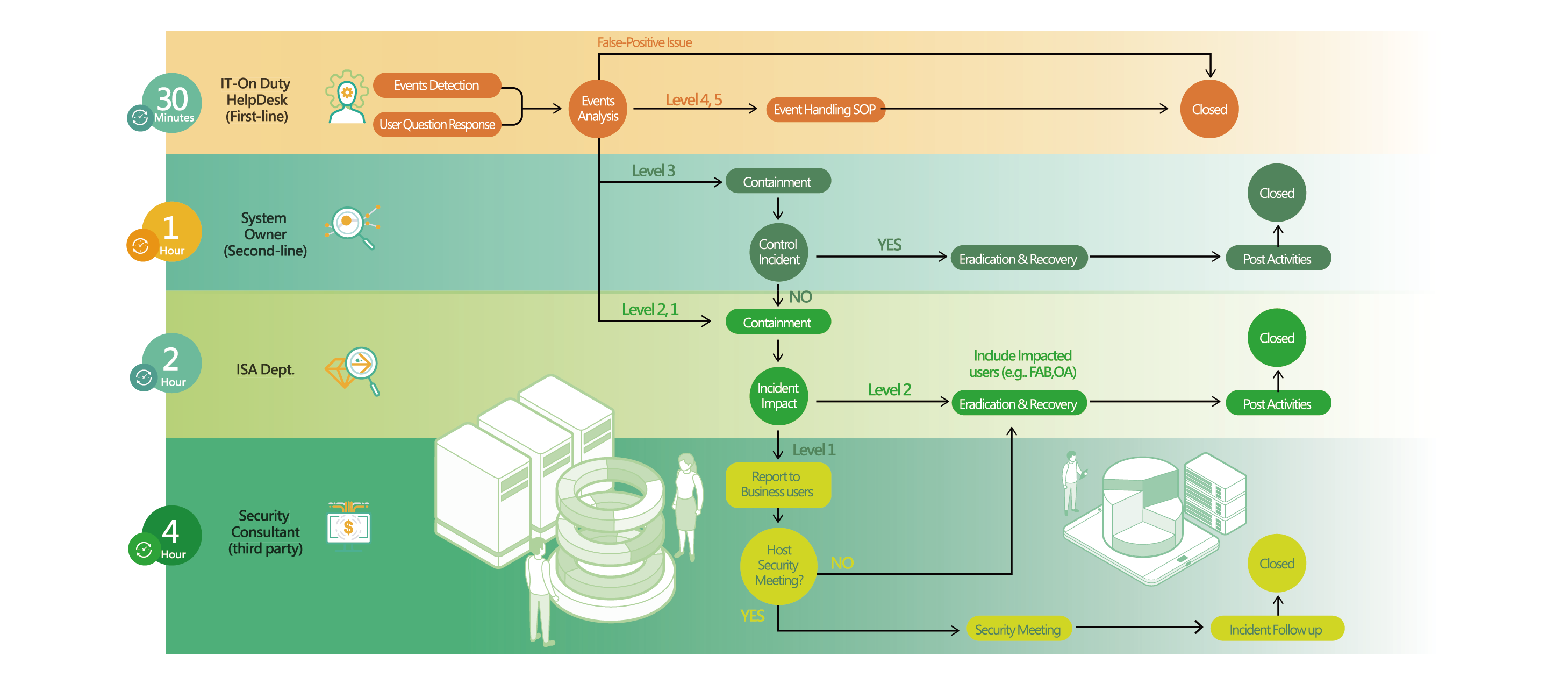
In addition, to ensure that important operations are not affected by failure of the information system in the event of natural disasters, man-made disasters, or virus infections of the organization, the Company established internal reporting procedures for earthquakes, fires, power blackouts, information system incidents, environmental safety and health incidents, and company reputation incidents (as shown below). In the event of a crisis, employees shall determine the person responsible for immediate reporting and the reporting level for each type of crisis based on the level of impact on operations. Where necessary, they must eport the incident to the President to activate emergency response measures and minimize losses.
Emergency response procedures