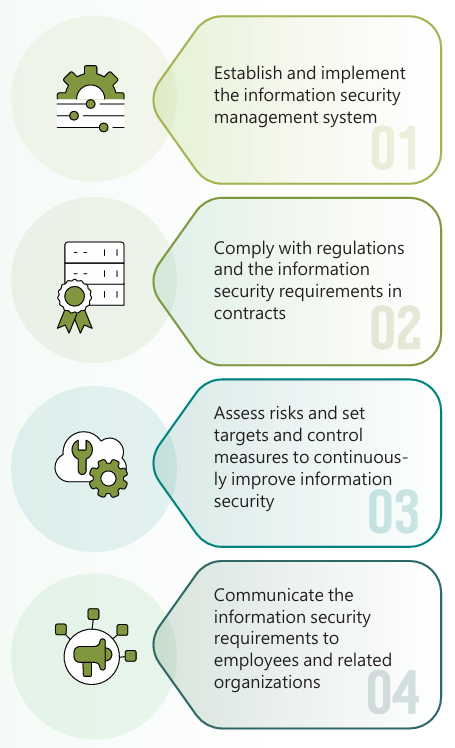
VisEra established information security management regulations based on ISO 27001 standards. We are committed to promoting information security, protecting and maintaining customer design and related information, and continuous improvements to meet the following targets in the requirements of the Information Security Policy:
8.6.1 Information Security Management Framework
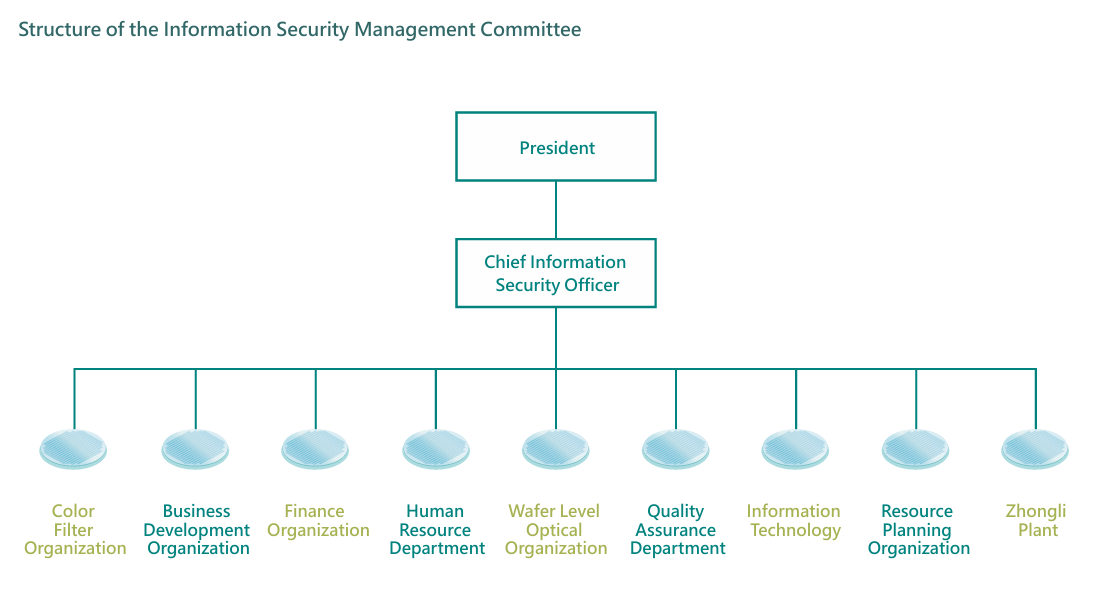
We established the "Information Security Management Committee" for implementing information security management operations to maintain the Company's competitiveness, reduce the risks of business disruptions, ensure that the information system meets confidentiality, integrity, and availability requirements, and strengthen employees' information security awareness. We assigned a dedicated information security supervisor and dedicated information security personnel to promote, coordinate, supervise, and review information security management matters. We established an information security incident notification and response organization to identify information security risks and implement information security risk improvement measures. Update the Chief Information Officer regularly on cybersecurity-related activities and event records. The Chief Information Officer reports cybersecurity governance achievements to the General Manager on a monthly basis. During the monthly project meeting, the Information Department advocates key cybersecurity control initiatives to both the Fab plant area and supporting units. Cybersecurity incident case studies are announced monthly on the company's intranet to raise awareness among colleagues.
8.6.2 Information Security Protection Measures
To strengthen information security, VisEra uses the six major aspects including cloud security, Demilitarized Zone (DMZ) security, information security governance, office area security, data center security, and production line and supplier security to strengthen the defenses for information security.
Note: For more details about Information Security Protection Measures, please refer to VisEra official website/ESG/ Governance/Information Security Management
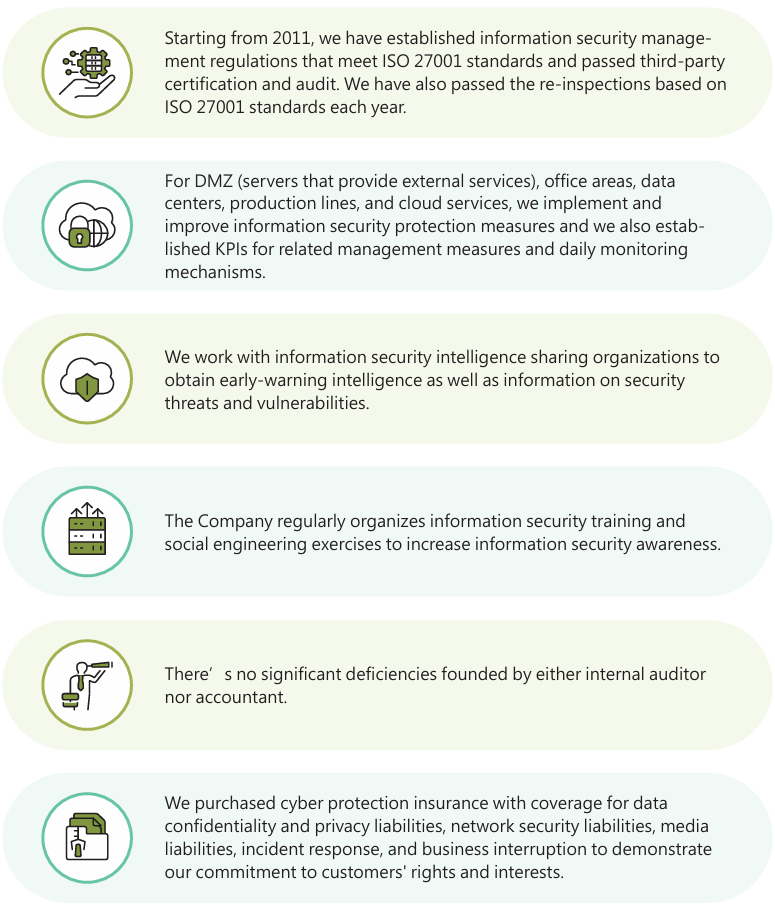
To effectively monitor information security intelligence, the Information Security System O&M Unit of VisEra's Information Technology Department uses the information security products and intelligence of renowned domestic and foreign companies such as Fortinet, TrendMicro, Crowd Strike, Palo Alto Networks, and Proofpoint. It established the Security Operation Center (SOC) in 2020 to monitor changes in the internal information security environment, actively detect information security problems, and take response measures for data centers, anti-virus protection, networks, operating systems, applications, and production line machine protection. We also work with the Science Park Information Security Sharing and Analysis Center to collect, exchange, and analyze information on information security risks for critical infrastructure. We monitor potential security threats and vulnerabilities and address the vulnerabilities to prevent potential threats with the security intelligence we obtained and reduce the risks of major information security incidents. After the establishment of the SOC, it monitors the use of the Internet, gateways, servers, and terminals each day. If it identifies suspected attacks from an external IP, it blocks the source IP. In 2023, CrowdStrike's Managed Detection and Response (MDR) service continued to be utilized for monitoring potential threats and responding to them. It aided in monitoring both office computers and IT server rooms for signs of malware infiltration. Cloud Machine Learning assisted in detecting and preventing the execution of malicious programs. Since its implementation, the system has successfully blocked medium to high-risk malicious software. There were no cybersecurity incidents reported in 2023.
To ensure compliance with the Company's Proprietary Information Protection Policy, the Proprietary Information Protection Officer (PIP Officer) inventories and classifies sensitive information such as proprietary information and personal data within the Company. Each unit sets up a special folder for personal data protection in the shared space with restricted data access and encryption. The PIP Officer performs quarterly self-audits to protect proprietary information and personal data.
In addition, to ensure that important operations are not affected by failure of the information system in the event of natural disasters, man-made disasters, or virus infections of the organization, the Company established internal reporting procedures for earthquakes, fires, power blackouts, information system incidents, environmental safety and health incidents, and company reputation incidents (as shown below). In the event of a crisis, employees shall determine the person responsible for immediate reporting and the reporting level for each type of crisis based on the level of impact on operations. Where necessary, they must eport the incident to the President to activate emergency response measures and minimize losses.
8.6.3 資訊安全推動成果
We established the "Information Security Management Committee" for implementing information security management operations to maintain the Company's competitiveness, reduce the risks of business disruptions, ensure that the information system meets confidentiality, integrity, and availability requirements, and strengthen employees' information security awareness. We assigned a dedicated information security supervisor and dedicated information security personnel to promote, coordinate, supervise, and review information security management matters. We established an information security incident notification and response organization to identify information security risks and implement information security risk improvement measures. Update the Chief Information Officer regularly on cybersecurity-related activities and event records. The Chief Information Officer reports cybersecurity governance achievements to the General Manager on a monthly basis. During the monthly project meeting, the Information Department advocates key cybersecurity control initiatives to both the Fab plant area and supporting units. Cybersecurity incident case studies are announced monthly on the company's intranet to raise awareness among colleagues.
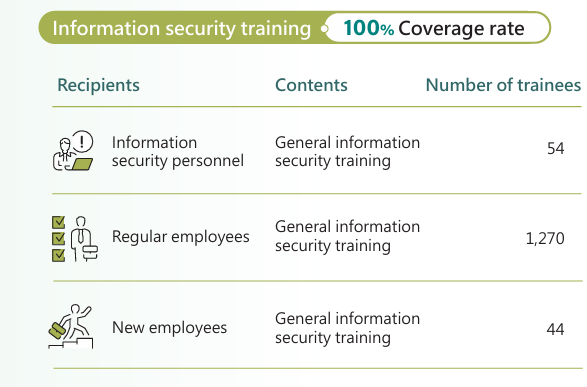

Spotlight
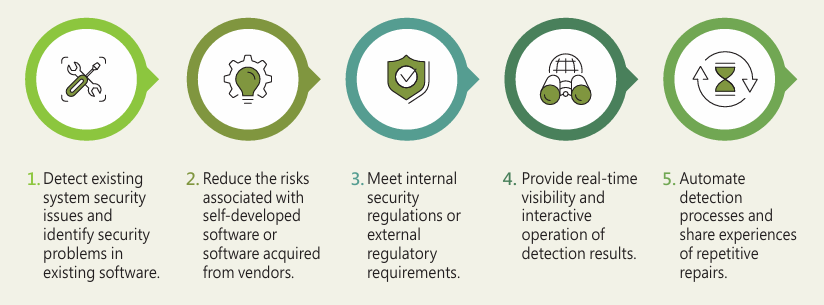
With the expansion of the scope of information technology applications, many business activities are being developed through information systems to enhance efficiency. However, as information systems are developed, improper syntax usage in programming has gradually become a source of system vulnerabilities exploited by hackers. Security incidents involving hackers exploiting software vulnerabilities for attacks and data theft are increasing. Moreover, with the tightening schedules of software development and maintenance personnel during the software development lifecycle, the difficulty of security management is also increasing. The ability to identify software security risks quickly and accurately is particularly important. Therefore, Jadeite Corporation has introduced a source code scanning platform.
The source code scanning platform helps developers detect potential security vulnerabilities in the source code. By using the source code scanning tool, hidden security weaknesses in the application are listed. Coupled with security consultants analyzing the causes and providing professional improvement suggestions, application developers can quickly and accurately fix the program's security weaknesses and vulnerabilities. This allows developers to promptly resolve security issues, reduce risks caused by source code vulnerabilities, and enhance the application's defense capabilities.
Through the source code scanning platform, security vulnerabilities are eliminated from the source, achieving the following goals in risk management during system development: